Salesforce Security Best Practices: Threat Update & Proactive Protection Tips
What’s Happening?
In the age of AI, data is the new gold. That makes Salesforce orgs the new gold vaults. Since early 2023, malicious activity targeting the riches within these vaults has been on a steady rise.
Specifically in 2025, the ecosystem experienced a dramatic increase in social engineering attacks around the commonly used Dataloader.io bulk import tool. This resulted in costly losses for a few unlucky customers.
What Can You Do About It?
In response, Salesforce increased its efforts to get customers to take proactive action. To help, we compiled this list of the most common threats, plus priceless prevention tips.
Want to be proactive, but don’t want to go down the security settings rabbit hole? Our Wolfpack has done this many times before and is standing by to help if you need it. Delegate it to us and get on with your day.
Threat Update
Below is a summary of 4 common threats currently facing Salesforce customers.
1: Social Engineering via Malicious Data Loader Tools
Summary:
In early 2025, threat actor UNC6040 deployed a voice-phishing campaign impersonating IT staff to trick employees into installing a malicious version of Salesforce Data Loader. Attackers are impersonating IT support teams and tricking users or third-party contractors into visiting malicious login pages or installing deceptive connected apps.
Potential Consequences:
Post-infection, attackers gained authenticated access to Salesforce environments, exfiltrated sensitive records, and later pivoted to other systems. Such access enabled data theft, extortion attempts, widespread lateral movement, and cloud-wide compromise.
2: AI-Specific Threats: Data Poisoning & Insecure Agents
Summary:
As Salesforce and its customers increasingly adopt AI agents, concerns have emerged around the poisoning of AI training data and vulnerabilities within autonomous execution environments
Potential Consequences:
Poisoned models can produce inaccurate outputs or leak proprietary data, leading to compliance failures, strategic missteps, and automated policy violations. As autonomy grows, exploiting AI agent workflows can cause hard-to-detect breaches or malicious actions at scale.
3: Operational Lapses & Burnout Leading to Hygiene Failure
Summary:
A resurgence of older malware and infostealers (e.g., Lumma, Mirai), combined with patching delays and human fatigue, is contributing to more successful basic attacks.
Potential Consequences:
Anyone user with access to export reports can stealthily siphon off valuable data. If a System Administrator user becomes compromised, the entire org is at risk.
4: Reliance on Outdated/Insecure Integrated Software
Summary:
Around 32% of cyberattacks still exploit unpatched software vulnerabilities. Custom Salesforce integrations and legacy middleware may introduce similar risks.
Potential Consequences:
Exploited software issues can lead to remote code execution, full org takeovers, and service disruption. Downtime can translate into significant financial losses and stress while exposing sensitive data.
Proactive Protection Tips
Get a Backup App
This is the single most important tip. Even if you don’t do anything else, this one action can save you like nothing else can.
Do not rely on native .CSV data “backups”. They provide a false sense of security.
If you’ve ever tried to perform a bulk import through Dataloader.io using a .CSV file, you know how challenging it can be when everything doesn’t line up perfectly.
Now imagine trying to do this for every single record in your org, while everyone is freaking out.
Salesforce pushes their latest acquisition Own Backup, but Wolfic can get you an even better tool for 33% less. Just ask!
Limit Who Can Export Your Data Using Reports
Not everyone needs this ability, and some may use it to export valuable data “just in case’ they get fired or decide to leave.
To manage this, check Setup > Profiles > choose one > click System Permissions > Edit > search for “Export” > uncheck the box for “Export Reports” > click Save. Repeat for each Profile that is assigned to an active User.
Pro tip: If someone asks to be able to export, see if you can instead subscribe them to the report. That way they get it in their email on a recurring basis, but can’t modify and export it anytime they want.
If someone who is not a System Administrator needs to export reports, grant them the permission using a Permission Set instead of adding it to their Profile. This gives you more granular control, and you can even set it to expire automatically after a certain amount of time.
Standardize Your User Deactivation Protocol
We’ve seen it on an alarmingly consistent basis: employees will try to siphon off as much data as possible as soon as they realize they’re probably about to lose access.
Data is the new gold, and your competitors would probably love to get their hands on all of yours.
To prevent this, the very first step is to go to the User’s record and uncheck the “Active” checkbox. This immediately locks them out.
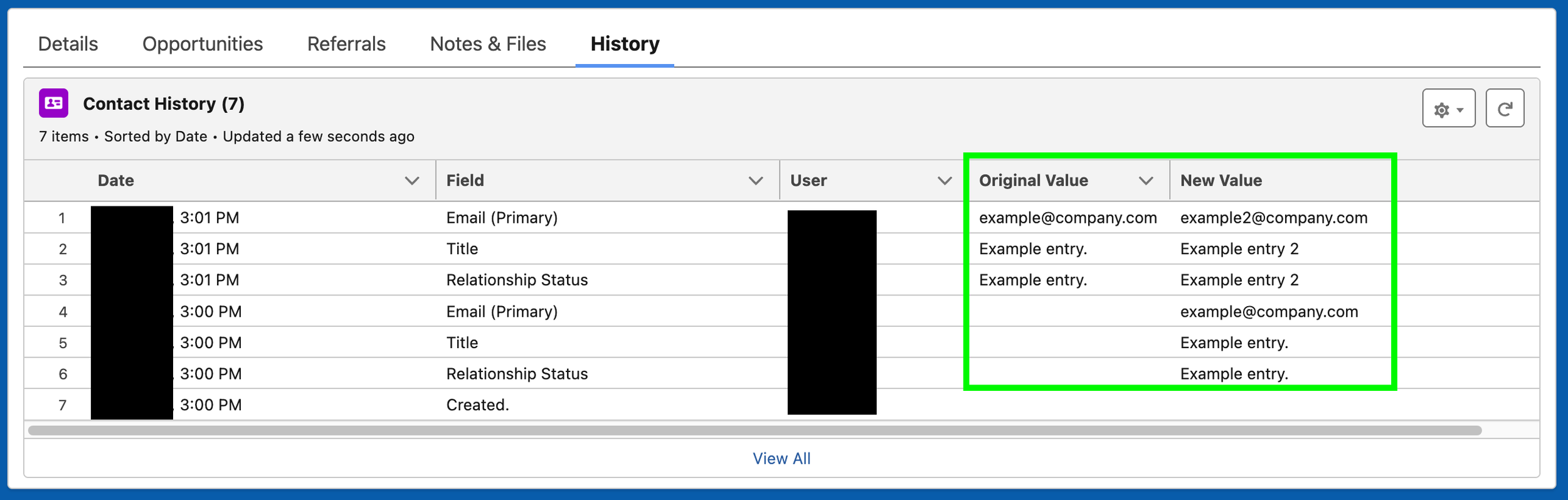
Unlock Field History Tracking for All Used Objects
This will allow you to see who makes edits to fields, when, and what the old and new values are. It also unlocks new Report Types which can help you selectively bulk restore old field values if needed.
For each Object you use, go to Object Manager > Fields & Relationships > click the “Set History Tracking” button in the top right hand corner. Then select up to 20 fields that are the most important, and click Save.
Navigate to Object Manager > Page Layouts > select each page layout that is in use. Click the Related Lists section within the left hand menu of the box at the top of the page. Search for “History” and then drag the component for “OBJECT History” down into the Related Lists section below.
If you don’t see the History related list appear on your record page, navigate to a record > click the Setup gear icon > select Edit Page. Then search for “Related List - Single’ and drag it onto your page. Click the new component and then use the Related List dropdown on the right hand side to select the “OBJECT History” List.
Pro tip: Change the Related List Type to “Enhanced List” and the Number of Records to Display to the maximum amount, 30.
Enforce Multi-Factor Authentication (MFA)
Encourage use of the native Salesforce Authenticator app unless your organization has purchased an alternative.
Leverage Salesforce’s MFA Enforcement Monitor to identify users not yet enrolled.
Go to Setup > Session Settings and ensure MFA is required for all users.
Reference the Salesforce Multi-Factor Authentication Implementation FAQ + Guide as needed.
Restrict Login IP Ranges
Define IP ranges associated with your corporate network and VPN.
Navigate to Setup > Profiles > choose one > Login IP Ranges > update and save. Repeat for all Profiles assigned to an active User.
Check Your Setup Audit Trail Regularly
Navigate to Setup > View Setup Audit Trail
This shows you exactly what settings were changed, when, and by whom.
Pro tip: Use the small link at the bottom titled “Download setup audit trail for last six months” to get a .CSV file of the audit trail.
Upgrade Option: Set up Real-Time Event Monitoring (requires Salesforce Shield):
Go to Setup > Event Monitoring Settings and enable critical event types.
Use Transaction Security Policies to trigger alerts or block behavior:
Setup > Transaction Security Policies > Create New Policy.
User Training & Phishing Awareness
Train users to:
Never share login credentials.
Confirm requests through internal channels.
Avoid clicking on unfamiliar links or attachments.
Emphasize that Salesforce Support will never call to request login information or instruct you to install apps.
Update Your Primary Contact
This is the person who will always be notified if something bad happens.
You don’t want it to be an inactive User.
Navigate to Setup > Company Information > Edit > ensure that the user in the Primary Contact field is correct
Always Apply the Principle of Least Privilege
Folks only need access to the functionality that they use to perform their role. Make it the norm that it’s not personal when they are denied access to functionality they don’t need.
Use Permission Sets and Profile Settings to grant only essential access.
Navigate to Setup > Profiles or Permission Sets, and remove unnecessary permissions.
One especially important permission is the ability to manage connected apps, since they can often modify your data.
Go to Setup > App Manager > Connected Apps OAuth Usage and review who has access.
Check the Official Trust Site First If Anything Seems Fishy
First, navigate to Setup > Company Information and search for “Instance”. This is where your data is actually stored.
Then use your Instance number to search the trust site for the latest updates affecting your org.
Pro tip: subscribe to receive email updates automatically.
An Ounce of Prevention
The spike in malicious activity around Salesforce—including the surge in Dataloader.io social engineering attacks—underscores a critical truth: relying on default workflows without robust safeguards is no longer an option.
Fortunately, you’re not navigating this alone. Salesforce has ramped up its proactive measures, and with Wolfic’s curated threat breakdown and practical prevention strategies, your team can act with precision and foresight.
If digging into security settings isn’t where you want to spend your time, our Wolfpack is ready—seasoned in Salesforce defense and primed to jump in when you need a trusted partner. Let’s build your resilience together.
Pro tip: Remember that you can also now Ask Salesforce’s Free AI Support Bot your questions! It’ll at least point you in the right direction or help clarify what you need.